Custom IT Strategy for Portland Businesses: Manufacturers & Professional Services
In today’s digital-first business environment, having the right technology isn’t just an advantage—it’s essential for survival. Portland businesses face unique challenges that require tailored technology solutions, not one-size-fits-all approaches. Whether you’re a manufacturing plant on the industrial eastside or a law firm downtown in Pioneer Square, your IT strategy must align with your specific goals, industry demands, and growth trajectory.
This comprehensive guide explores how manufacturers and professional service businesses across Portland can develop custom IT strategies that address their unique challenges, maximize operational efficiency, and secure their digital assets in an increasingly complex technology landscape.
Understanding Portland’s Business Technology Landscape
The Unique Technology Needs of Portland Industries
Portland’s business ecosystem is diverse—from advanced manufacturing operations to specialized professional service firms. Each sector faces distinct technology challenges:
- Manufacturing companies require systems that integrate production workflows, inventory management, and supply chain visibility
- Law firms need secure document and case management, client portals, and compliance-ready systems
- Architectural firms depend on powerful design software, rendering capabilities, and collaborative platforms
- Engineering businesses rely on specialized technical applications and data-intensive workflows
- Consulting organizations require flexible systems that support remote collaboration and client engagement
While national technology trends matter, Portland businesses must navigate specific local factors, including the region’s talent market, connectivity infrastructure, and competitive landscape.
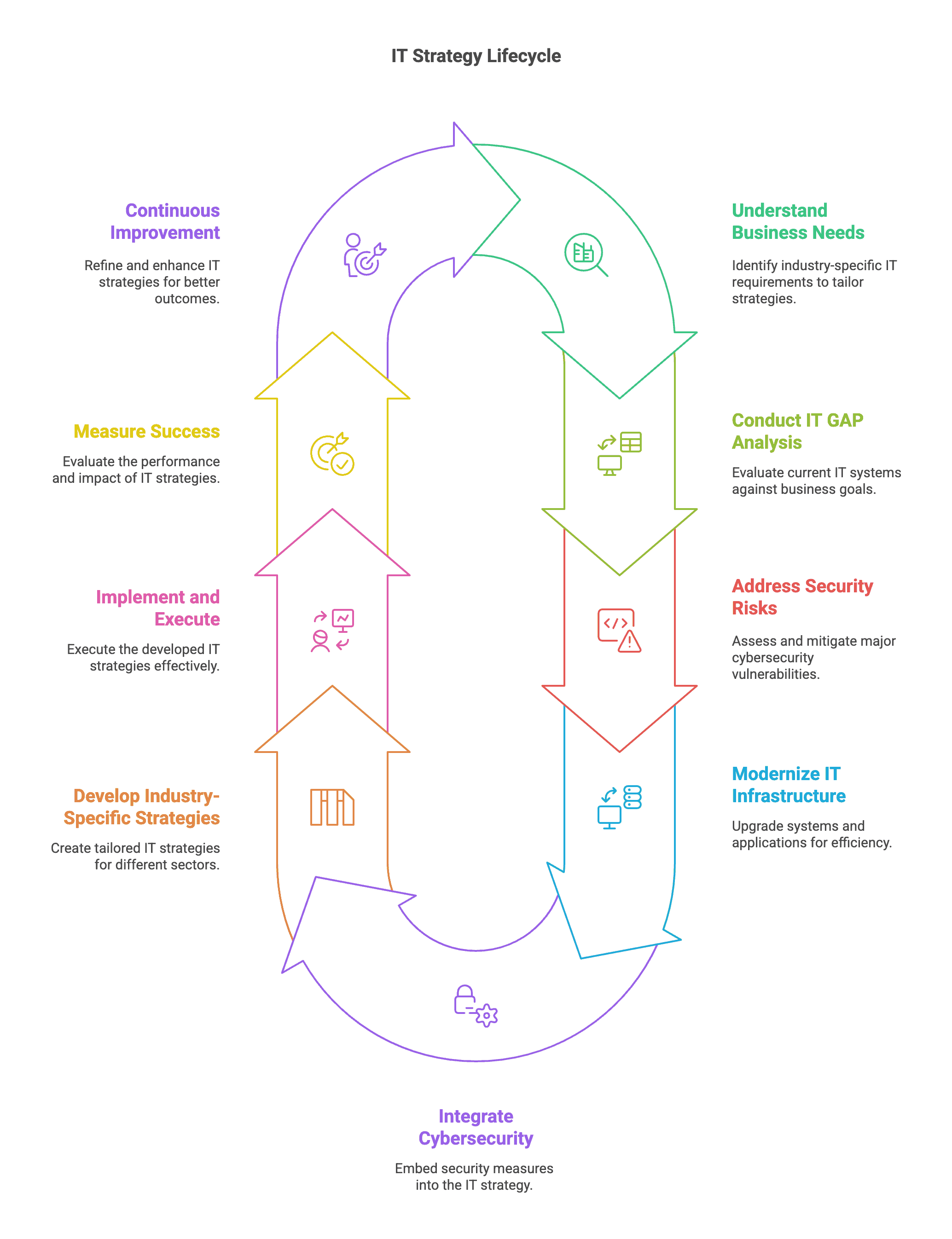
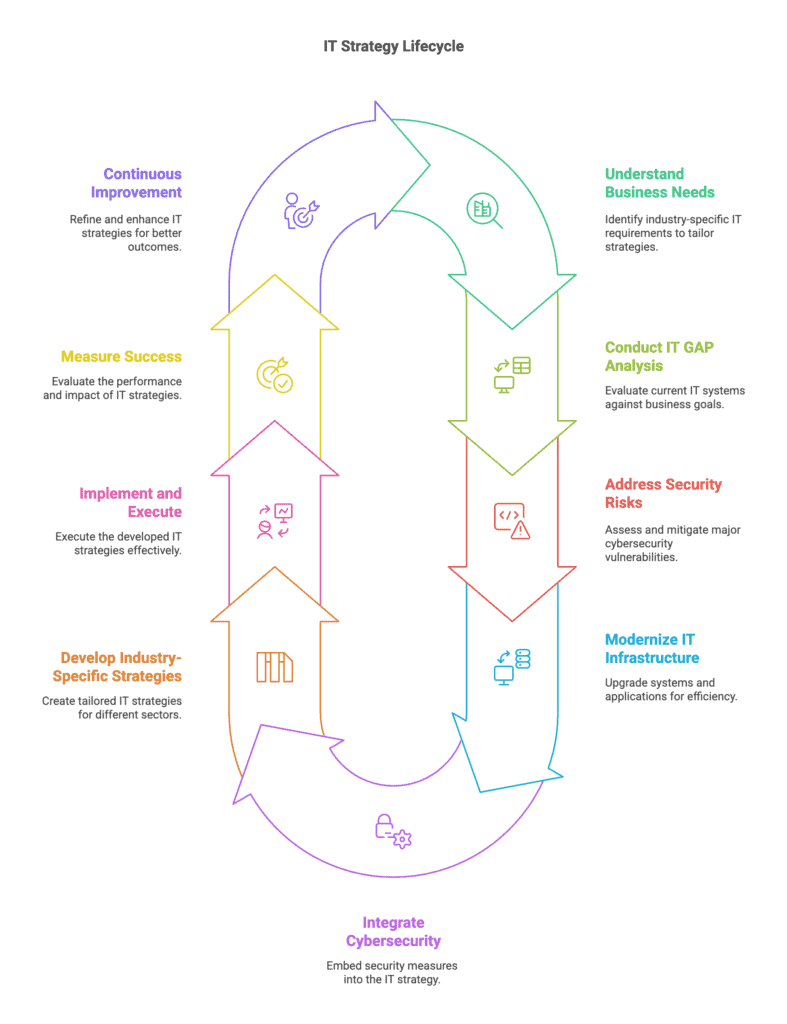
The Foundation: IT GAP Analysis for Portland Businesses
What Is an IT GAP Analysis?
An IT GAP Analysis serves as the cornerstone of any effective IT strategy. This systematic assessment compares your current technology capabilities against your business objectives and industry requirements, identifying:
- Underperforming systems that limit productivity
- Missing capabilities required for future growth
- Redundant technologies that increase costs without adding value
- Security vulnerabilities that put your business at risk
For Portland businesses, an IT GAP Analysis provides crucial insight into how your current technology stack measures against both your strategic goals and local industry standards.
Conducting an Effective IT GAP Analysis
A comprehensive IT GAP Analysis for Portland businesses typically involves:
- Documentation of current systems: Inventory all hardware, software, networking equipment, and cloud services
- Business goals alignment: Map how current technology supports (or hinders) critical business objectives
- Industry benchmarking: Compare your capabilities against Portland competitors and industry standards
- User experience evaluation: Gather feedback from staff about technology pain points and needs
- Future needs assessment: Identify upcoming business initiatives that will require technology support
This process reveals the “gaps” between your current capabilities and what your Portland business truly needs to succeed—forming the foundation for strategic technology planning.
From Analysis to Action
Once you’ve completed your IT GAP Analysis, prioritize identified issues based on:
- Business impact (how significantly they affect operations)
- Security implications (potential risk exposure)
- Cost considerations (both investment required and potential savings)
- Implementation complexity (time and resources needed)
This prioritization ensures your custom IT strategy addresses the most critical needs first, maximizing the return on your technology investments.
Modernization: Creating Your Custom IT Modernization Strategy
Signs Your Portland Business Needs IT Modernization
Portland businesses often display clear warning signs when their technology infrastructure requires modernization:
- Systems frequently crash or operate slowly
- Staff rely on manual workarounds for routine tasks
- Increasing maintenance costs for legacy systems
- Inability to support remote or hybrid work models
- Difficulty integrating with customer or vendor systems
- Falling behind competitors in technology capabilities
If these symptoms sound familiar, it’s time to develop a targeted IT Modernization Strategy.
Core Components of an IT Modernization Strategy
Infrastructure Modernization
Evaluate whether your current hardware, networking equipment, and facilities meet business needs. Consider:
- Cloud migration opportunities that reduce on-premise infrastructure
- Network upgrades to support modern applications and workflows
- Modernized data storage solutions that improve accessibility and security
Application Modernization
Review your software portfolio for modernization opportunities:
- Replace legacy applications with modern cloud-based alternatives
- Integrate disparate systems to improve data flow
- Implement APIs to connect critical business systems
- Automate manual processes through workflow software
Digital Experience Modernization
Enhance how employees and customers interact with your technology:
- Improve user interfaces for internal systems
- Develop mobile capabilities for field-based staff
- Create customer-facing digital tools that streamline interactions
- Implement self-service portals for common requests
Phased Implementation Approach
For Portland manufacturers and professional service firms, a phased modernization approach typically works best:
- Phase 1: Address critical vulnerabilities and immediate business needs
- Phase 2: Implement core system improvements that enhance daily operations
- Phase 3: Deploy advanced capabilities that provide competitive advantages
- Phase 4: Establish continuous improvement processes for ongoing modernization
This sequential approach manages risk while delivering incremental benefits throughout the modernization journey.
Cybersecurity: Integrating Risk Assessments into Your IT Strategy
The Portland Cybersecurity Landscape
Portland businesses face an evolving set of cybersecurity challenges:
- Targeted ransomware attacks against local businesses
- Increasing compliance requirements across industries
- Supply chain vulnerabilities that affect manufacturers
- Client confidentiality concerns for professional service firms
- Advanced persistent threats targeting intellectual property
A custom IT strategy for must include robust cybersecurity measures tailored to your specific risk profile and industry requirements.
The Cybersecurity Risk Assessment Process
A comprehensive Cybersecurity Risk Assessment typically includes:
- Asset inventory: Documenting all systems, data repositories, and access points
- Threat analysis: Identifying potential threats specific to your business and industry
- Vulnerability assessment: Evaluating weaknesses in your current security posture
- Impact analysis: Determining potential business consequences of security breaches
- Risk prioritization: Ranking identified risks based on likelihood and potential impact
- Mitigation planning: Developing specific strategies to address priority risks
This assessment should consider local factors like physical security at your facilities, regional cybersecurity resources, and Portland-specific regulatory requirements.
Building Security Into Your IT Strategy
Based on your Cybersecurity Risk Assessment, integrate these security elements into your broader IT strategy:
- Security architecture: Design systems with security controls built in from the start
- Access management: Implement role-based access controls and multi-factor authentication
- Data protection: Develop comprehensive data classification and protection mechanisms
- Incident response: Create detailed plans for responding to security incidents
- Security awareness: Train employees on security best practices and threat recognition
- Continuous monitoring: Implement systems to detect and alert on security anomalies
By approaching security as an integral component of your IT strategy rather than an afterthought, Portland businesses can protect valuable assets while enabling operational efficiency.
Industry-Specific IT Strategy Insights
Custom IT Strategies for Manufacturers
Portland’s manufacturing sector—from metal fabrication to advanced electronics—requires specialized technology approaches:
- Production systems integration: Connect shop floor equipment with management systems
- Supply chain visibility: Implement real-time tracking and forecasting capabilities
- Quality assurance technology: Deploy systems to monitor and improve product quality
- Predictive maintenance: Use IoT sensors and analytics to prevent equipment failures
- Workforce enablement: Provide digital tools that enhance worker productivity and safety
Custom IT Strategies for Professional Services
For Portland’s law firms, architectural practices, engineering companies, and consultancies, effective IT strategies typically emphasize:
- Client collaboration: Secure platforms for sharing deliverables and communicating
- Knowledge management: Systems to capture, organize, and leverage institutional expertise
- Project management: Integrated tools to track timelines, resources, and deliverables
- Secure mobility: Solutions that enable secure work from anywhere
- Business intelligence: Analytics capabilities to measure performance and identify opportunities
Implementation: Bringing Your Custom IT Strategy to Life
Creating Your Implementation Roadmap
Translating strategy into action requires a detailed implementation roadmap that includes:
- Project phases with clear timelines and milestones
- Resource allocation (both internal staff and external partners)
- Budget projections and financial tracking mechanisms
- Risk management provisions for implementation challenges
- Change management procedures to ensure adoption
For Portland businesses, consider how seasonal factors, local talent availability, and regional business cycles might affect your implementation timeline.
Measuring Success: Key Performance Indicators
Establish clear metrics to evaluate your IT strategy’s effectiveness, such as:
- System uptime and reliability statistics
- User adoption and satisfaction measures
- Process efficiency improvements
- Security incident frequency and resolution times
- Direct cost savings and revenue impacts
- Competitive advantage indicators
Review these metrics regularly, adjusting your strategy as needed to maximize business impact.
Building the Right Team
Executing your IT strategy requires the right mix of talent and expertise:
- Internal IT team: Ensure your staff has the necessary skills and capacity
- Technology partners: Identify vendors who understand your industry and business
- Managed service providers: Consider Portland-based MSPs for ongoing support
- Cybersecurity specialists: Engage experts for security implementation and testing
- Change management resources: Support user adoption through training and communication
In Portland’s competitive technology talent market, consider how your staffing approach balances in-house capabilities with external expertise.
Conclusion: The Path Forward
Developing a Custom IT Strategy isn’t just about technology—it’s about creating a foundation for sustainable business success. By conducting a thorough IT GAP Analysis, implementing a thoughtful IT Modernization Strategy, and prioritizing Cybersecurity Risk Assessments, your organization can transform technology from a necessary expense into a strategic advantage.
The most successful Portland businesses recognize that technology strategy isn’t a one-time project but an ongoing process of alignment, optimization, and innovation. As your business evolves and technology continues to advance, your IT strategy should adapt accordingly.
Now is the time to evaluate your current technology approach and consider how a truly customized IT strategy could help your business achieve its full potential.