Portland Accounting IT Solutions: Benefits of IT Management for CPAs
Proactive IT management is a strategic approach that anticipates and addresses potential issues in IT infrastructure before they escalate into...
6 min read
Nick : Updated on July 24, 2025

The way we work has changed, and so have the risks. With employees now splitting time between home and office, hybrid work offers greater flexibility. But it is also susceptible to cybersecurity threats.
From unsecured Wi-Fi networks to unmanaged personal devices, businesses are facing several vulnerabilities that traditional security models aren’t equipped to handle.
In fact, 68% of cybersecurity experts believe remote work has made their organizations more vulnerable to cyber threats. But eliminating hybrid work altogether isn’t the answer, as 35% of remote employees believe that working from home increases productivity.
The key is to adapt. You have to rethink how your business protects data, devices, and access in a distributed environment.
This blog explores the cybersecurity risks in remote and hybrid setups, along with proven best practices to help you stay secure without sacrificing flexibility.
Table of Contents:1. How Remote Employees Are Targeted
2. Breaking Down Remote Work Risks
3. Cybersecurity Policies and Tools That Enhance Security
4. The Employer’s Role in Security 5. Key Takeaways 6. Conclusion 7. FAQs |
Cybercriminals see remote employees as easy targets, as they are often outside the reach of standard security controls. They exploit common habits and vulnerabilities via increasingly sophisticated tactics to breach systems, steal data, and gain unauthorized access.
Here are the most common methods they use:
Man-in-the-middle attacks occur when cybercriminals place themselves between two parties, such as a user and an app or website. This allows them to steal identities, commit financial fraud, make unauthorized purchases, and more.
Phishing attacks cause 36% of data breaches. These scams often begin with fake emails or messages that trick employees into sharing their login details. They can be especially deceptive because they usually appear to come from trusted colleagues or partners.
Attackers manipulate employees with psychological influence into revealing confidential information or granting access.
In Q1 2025, 2,289 ransomware attacks were reported. These attacks use malicious software to encrypt files and demand a ransom for their release. Remote devices, with weaker security, are often more vulnerable to such threats.
As hybrid work becomes the norm, the boundaries of corporate security are harder to define. Traditional defenses, built around centralized offices and company-managed devices, seem to be insufficient. They no longer cover the full scope of how, where, and with what tools employees work.
Therefore, it is essential to understand the unique vulnerabilities associated with remote environments and follow cybersecurity best practices. You need to strike the right balance between keeping data safe and letting employees work remotely.
Below are the biggest challenges your business needs to assess and how to proactively reduce the risk:
60% of remote workers use unsecured home Wi-Fi, exposing sensitive data to cyber threats. Unlike secured corporate networks, these networks are often poorly protected. This makes it easier for hackers to intercept data. It leads to potential cyber threats and breaches.
Solution:
53% of employees use the same password across different devices. When employees skip multi-factor authentication (MFA) or use weak, repeated passwords, it makes it simple for cyber attackers to target data.
Solution:
Personal laptops, smartphones, or tablets used for work often lack proper security controls. Without management tools, IT teams cannot keep the devices protected.
Solution:
Working remotely affects compliance with laws like GDPR or industry-specific regulations. Data stored or accessed from insecure devices may lead to violations or legal consequences.
Also, cloud tools are great for remote work, but misconfigured settings are a top cause of breaches. When access isn’t controlled, anyone can get in.
Solution:
Without supervision, employees may accidentally or intentionally mishandle data. This can cause serious damage to the company's data.
Solution:
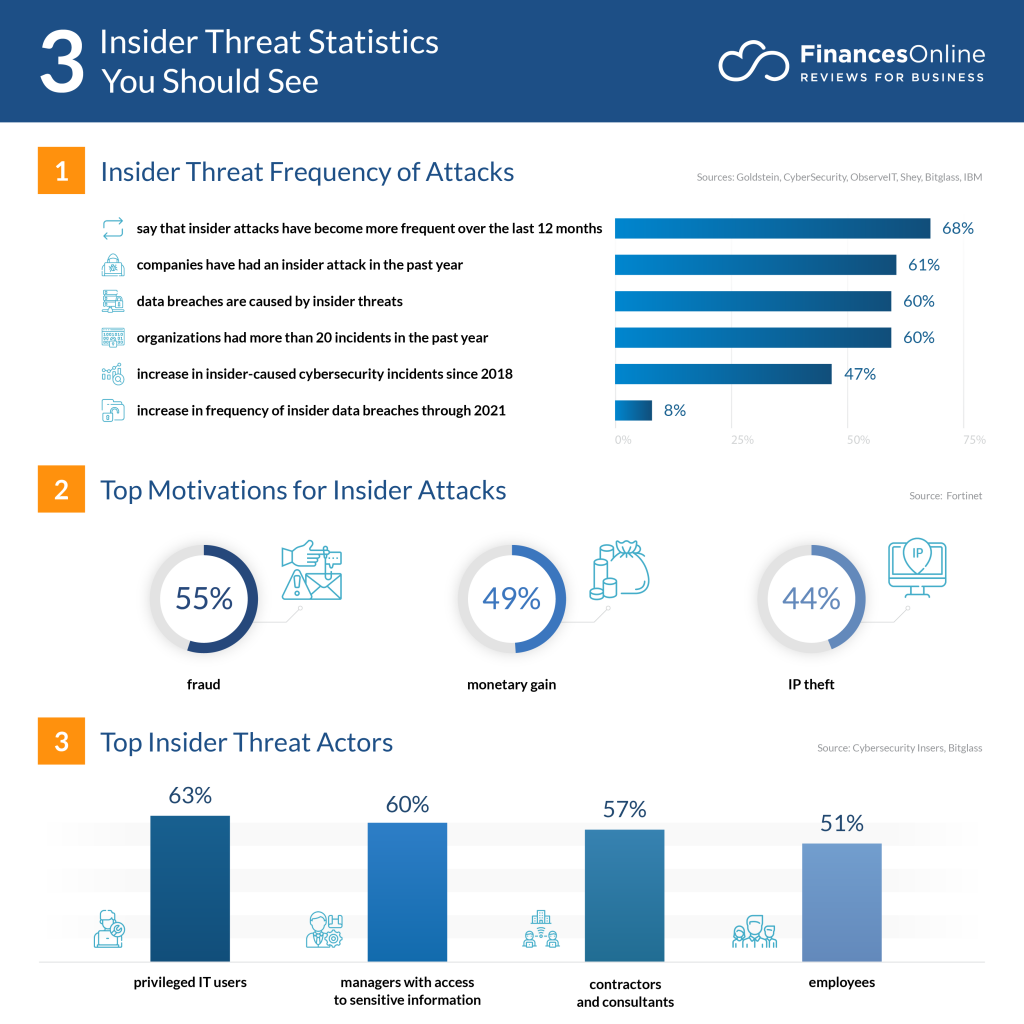
Shadow IT is when someone uses the hardware or software without the IT team knowing about it. When this happens, your IT team loses control over data security, increasing the risk of data leaks and non-compliance.
Solution:
Remote work means laptops and phones are often outside the office. If a device gets stolen and isn’t encrypted, your data is at risk.
Solution:
Data can leak when employees use unsecured networks. It may not be intentional, but it’s risky as it exposes confidential information beyond the work setting.
Solution:
A VPN protects your remote connections, but only if set up correctly. Poor configurations or unapproved VPN services create weak points that hackers can exploit.
A VPN keeps your data safe by encrypting it. But split tunneling is enabled in a lot of work settings. As a result, only some of the internet traffic goes through the VPN, while the rest doesn't. Hackers could use the unprotected traffic to attack the system.
Solution:
Hackers target platforms like Zoom, Slack, and Teams. If these platforms are poorly set up, outsiders can access meetings or steal data.
Solution:
To stay secure in a remote work setting, you need to do more than just follow best practices. Strong policies and the right tools work together to reduce risks and protect sensitive data. It's important to control how information is accessed, shared, and stored.
Here are the policies you should implement:
Create and manage your own encryption keys rather than using those provided by cloud service providers. This is particularly important for protecting highly sensitive data and maintaining control, ensuring confidentiality, and meeting compliance requirements.
Avoid security gaps caused by unverified productivity apps. Provide employees with approved collaboration, communication, and storage platforms that meet your security requirements. Also, keep on updating them to avoid security breaches.
Firewalls include app awareness, intrusion prevention, and threat protection. This enforces consistent security policies and reduces unauthorized access across remote work environments.
Cybersecurity is a team effort, but leadership sets the tone. Here’s what you must do:
Set clear security policies that define expectations and rules for remote work
Invest in infrastructure and tools that protect your digital assets without hindering productivity
30% of IT security professionals believe that phishing attacks, among other cyber threats, often succeed due to inadequate employee training. So, provide regular training so employees stay alert to evolving threats
Monitor for risks but respect privacy to maintain trust
Promote a security-first culture where everyone understands their role in keeping data safe
Hybrid work increases risks like data breaches and insider threats, with remote workers often targeted due to weak home security. Common issues include poor passwords, unmanaged devices, VPN flaws, and shadow IT.
Structured best practices like using VPNs, MFA, endpoint protection, and encryption can significantly reduce risks.
Always secure cloud and collaboration tools through access controls, CASBs, and regular permission audits.
Strong leadership is essential for driving cybersecurity. It's crucial to set clear policies, offer continuous training, and encourage a security-first culture.
Using company-approved tools and firewalls, along with BYOK policies, helps maintain control over sensitive data.
Proactive cybersecurity is essential for maintaining trust, productivity, and regulatory alignment in hybrid environments.
Cybersecurity is no longer just an IT issue; it’s a business imperative. The more proactive you are today, the fewer incidents you’ll have to react to tomorrow.
By adopting business cybersecurity best practices, the right tools and ongoing vigilance, you’ll build a resilient security foundation that supports both productivity and protection.
Heroic Tech helps protect your business from cybersecurity threats. Explore the solutions today and create a secure, efficient hybrid workplace.
Proactive IT management is a strategic approach that anticipates and addresses potential issues in IT infrastructure before they escalate into...

Remember when a simple password felt like enough to guard your digital kingdom? Those days are long gone. Industry research, including Verizon’s Data...

Picture this: It’s 2:00 PM on a Tuesday. You’ve just finished a heavy lunch, and now you’re sitting in a dimly lit conference room, or worse, staring...
Conflict in the workplace is sadly inevitable. Put a group of people in a room together for eight hours or longer every day, week after week. No...
The concept of remote work and Beaverton remote IT has gained tremendous momentum. Companies across various industries have embraced this shift,...
Millions of people around the world have leveraged the awesome power of WordPress to build their sites. Whether for personal or business use,...